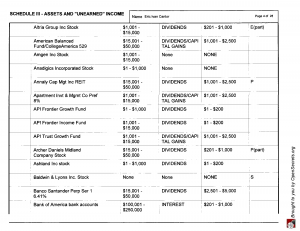
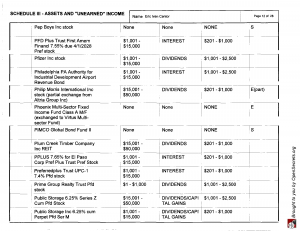
From Virginia Lawyers Weekly:
A hacker’s theft of millions of Virginia’s most sensitive prescription drug records isn’t slowing Sen. Mark Warner’s push for electronic medical records.
The former governor convened a conference in Richmond last week about the medical and cost-saving benefits of digitizing hundreds of millions of patient records nationally.
“We’ve been talking about this subject, policymakers have, for decades: how can we make sure that we can bring the power of information technology to our health care system,” Warner told reporters at Virginia Commonwealth University.
Warner, who made a fortune as an early investor in cell phones and information technology, was among the earliest apostles of e-medical records. The federal economic stimulus package that Warner supported provides nearly $20 billion to begin the process of digitizing medical records and sharing them over secure networks.
Here’s the money quote at the bottom of the story (read the whole thing still):
VITA [Virginia Information Technologies Agency] was Warner’s idea for consolidating the state’s disparate and far-flung computer networks and technology procurement systems under one agency. It went online during his term as governor from 2002 to 2006.
“You’re never going to have an infallible system. But … you’ve got to make sure that you learn if there are breaches like this and improve and protect the system,” he said.
Does anyone else feel so safe in the knowledge that the government (or even a business) is going to be responsible for retaining your complete medical record?
The story portrays Mark Warner has being so tech savvy but he shows by his own comments he doesn’t know jack about computer security. And notice that he mentions that you improve security on the system only after the data has been compromised.
And given how a bureaucracy responds to computer security problems, I feel even more secure: Consider how the Oklahoma Department of Corrections implemented their state-wide sex offender registry. They set up the system and how it communicated with the database in such a way that it was possible to change a few words in the URL of the web page and viola, you have the social security number of every person listed on the registry (The Register (UK), Daily WTF).
And when the author of the article at the Daily WTF alerted the Oklahoma DOC to the problem they responded by changing the SELECT term from “social_security_number” to “Social_Security_Number”. Just change the URL to the capitalized term and viola, the information was still available to anyone. The problem was only fixed when the author revealed to the Oklahoma DOC that not only was information available about people that were on the sex-offender registry, but information regarding DOC employees, including medical information, was also available.
The author also theorize that given the way the system was set-up, he could have added records to the tables, enabling him to add people as DOC employees or as sex-offenders.
If that’s the way the government is going to handle my medical records, no thanks.
And, of course, it isn’t just the government that has failed to address security concerns. According to the The Register, a prescription processing firm, Express Scripts, offered a $1,000,000 bounty for the return of personal information, including prescription information in some cases, that a group managed to download.
This also goes back to the nature of computer security. It’s a reactive process. Security flaws and exploits are not fixed until there’s a problem that has been documented. Hell, just look at every security vulnerability in any Microsoft product.
And normal citizens don’t give a damn about their security in most cases, and where do those people work? Some are bound to work in sensitive places. You still have people that either don’t bother with wireless network security on their routers, or if the do, they’re still using WEP which the FBI demonstrated could be cracked in three minutes back in 2005. And even the more secure WPA has been demonstrated to have security vulnerabilities.
And by no means am I saying that paper records in a doctor’s office are secure. But at least then it has to be an employee or a burglar that compromises the information. And it wouldn’t affect millions and millions of people if it does happen. It also would take a lot more time and effort to copy and distribute paper medical records than it would take for electric files. Even if you find the people that compromise an electronic medical record, that information could have been forwarded to a million people already.
And then you have situations where neither the government nor business disclose the fact that their information has been compromised. Was it Bank of America that failed to tell their customers that their personal information had been breached until six months after the incident occurred? And look at how the state of Virginia has been mum about what exactly was compromised with the hacking of their prescription drug database.
All around, this is a Charlie-Foxtrot waiting to happen.